In a nutshell: no! In this post we dig into the specifics of why – especially in OT – both solutions are not sufficient.
To set things straight: without any doubt, firewalls and a Security Information & Event Management (SIEM) system are relevant parts of a functioning, powerful intrusion detection system in both IT and OT. However, particularly in OT they have gaps and work best in combination with other OT-specific measures.
Firewalls
Firewalls are sitting at the network perimeter, look outwardly and only analyze (typically signature-based) traffic, that passes this perimeter via the respective gateway. They are typically made for enterprise IT networks.
This results in Firewalls being blind to:
- Suspicious communication WITHIN the OT network: Unlike IT networks, OT networks are relatively open due to existing processes. Malware or attackers can bypass firewalls and enter the OT via directly connected maintenance laptops or 1:1 connections via VPN remote access. To make matters worse, these access points are mostly used by external service providers or the support teams of the equipment vendors – with limited control by your own IT security team. Any malicious activity happening within a network is not detected and signaled by firewalls. In addition to restricting privileges and implementing strict authentication management, it is also necessary to monitor the network in order to track activities within the networks and investigate suspicious behavior.
- Attacks for which no signatures exist yet: The majority of firewalls used in OT are signature-based. This means that their detection capabilities depend on a library of known attack patterns, such as those that can be drawn up from malware that has already been analyzed. However, for years, the initial attack vector on corporate networks has been shifting toward novel or stealth attack techniques or attacks that do not require malware. This is confirmed by various time series from insurance and security companies.
In most cases, existing, often still unknown (so-called zero-day) vulnerabilities in hardware and software components are exploited for this purpose. Another method is to take over legitimate user accounts using stolen or fraudulently obtained access data (e.g., via spearphishing). The attackers thus move around the network as legitimate users. In both cases, the attackers remain invisible to the firewall because they are already behind it. Here, too, network monitoring creates visibility behind the firewall. Integrated anomaly detection also allows the detection of intrusion patterns and security-relevant communication behavior that are not covered by signatures.
- Living-off-the-land techniques: This type of attack attempts to get by completely without malware or other payloads. Instead, it uses the resources (systems, functions, protocols) available in the compromised network. These types of stealth attacks are even more difficult for signature-based security solutions to detect. Anomaly detection, on the other hand, can also make this attack technique visible.
- Attacks by internal perpetrators: see point 1.
- (Often) Communication using OT-specific protocols: OT is a big mixed bag when it comes to the protocols used. In addition to a large number of protocols familiar from IT, a wide variety of protocols specific to OT are used. In addition, many OT systems and components have proprietary vendor protocols. Firewalls are generally unable to detect or analyze these. For this reason, solutions that understand both IT and OT protocols are necessary—for example, a network-based intrusion detection system (NIDS) developed specifically for OT, such as Rhebo Industrial Protector.
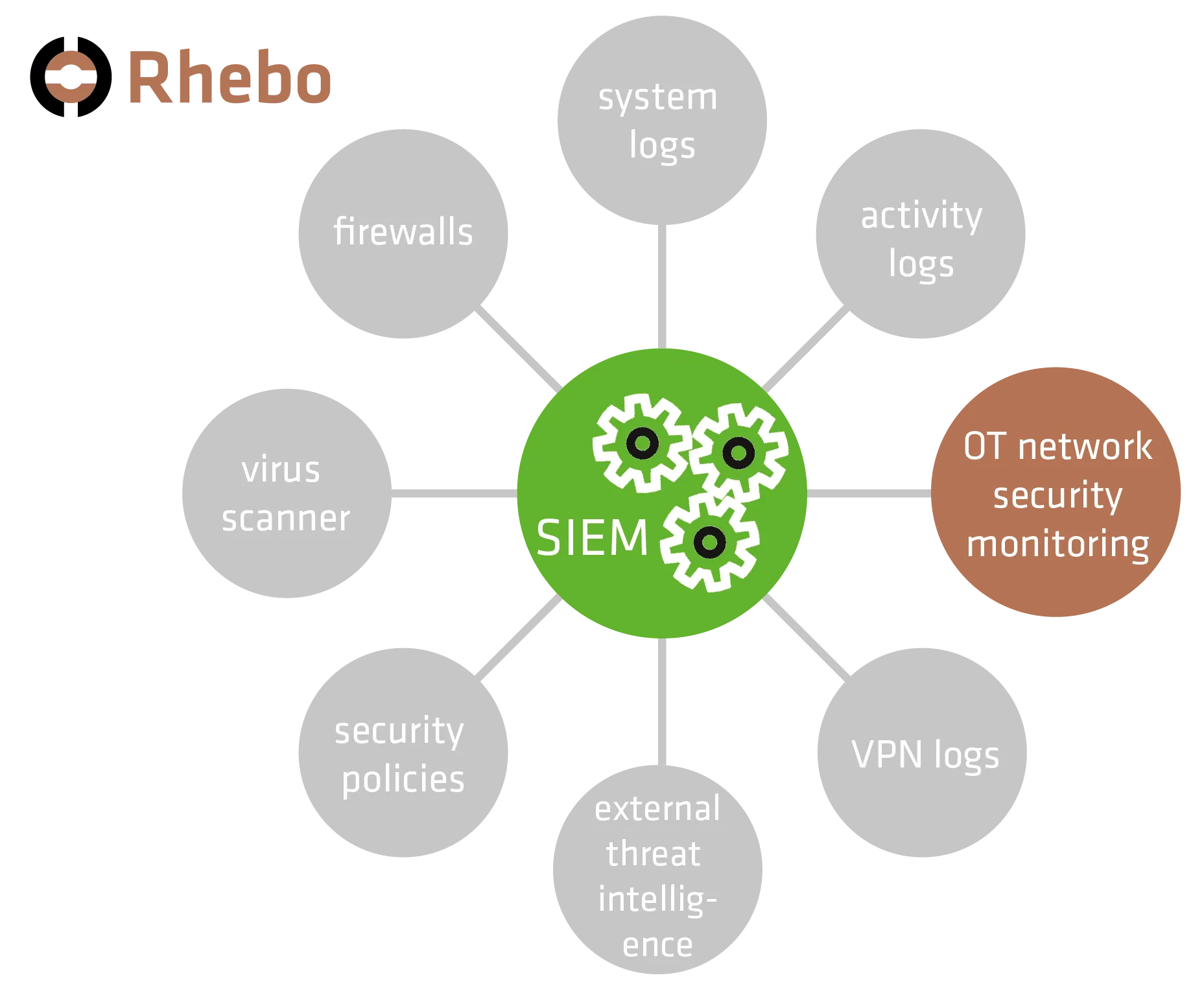
SIEM system
A SIEM system collects log data from various systems in the networks as well as threat intelligence information at a central location, analyzes it, and attempts to identify patterns that indicate a threat (Fig. 1). AI or machine learning is often used at this point to comb through the extensive data sets.
However, a SIEM alone is NOT an intrusion detection system, as it is dependent on its data sources. If data sources are missing, a SIEM can only detect/infer acute threats to a limited extent. Without log data or monitoring within the OT, even a SIEM has no insight into the OT networks and therefore cannot provide any information about the threat situation and OT security posture.
Conclusion
Firewalls and SIEM cannot save OT, either alone or in combination. They lack the insight, understanding, and specific functions that are essential for OT networks.
An OT monitoring system with integrated anomaly detection (also called network-based intrusion detection system) – such as Rhebo Industrial Protector – closes the security gaps and blind spots left open by firewalls and SIEM.
