On November 11, the German Federal Office for Information Security (BSI) published its annual report on cybersecurity in Germany. The findings confirm the trend toward increasingly covert cyberattacks. What this means for OT.
A key statement in the BSI's 2025 status report stands out in the section “Reported vulnerabilities in software products” in chapter “02 Attack surface”: “In particular, the lack of logging and monitoring mechanisms makes it difficult for companies to detect attacks in time and respond to them.”
This observation is particularly significant for OT as it is the general Achilles heel of industrial companies.
Signs of prepositioning
This starts with the number of advanced persistent threats (APTs) active in Europe. Germany and the UK are among the top 10 countries targeted by mostly state-sponsored APT groups. Twenty-eight APTs have their sights set on Germany, and 22 on the UK. This corresponds to 25% and 20 %, respectively, of the groups observed worldwide.
In its 2025 status report, the BSI hints at what Rhebo's Anne Grätz recently analyzed in her article “Why are there so few OT cyberattacks?”. So far, there have been no known acts of cyber sabotage on infrastructure, but there are increasing signs of prepositioning campaigns by state-sponsored APTs such as Sandworm and APT28. The facility may not be blowing up in the operator's face yet, but the attackers are already sitting deep in the network with their fingers on the trigger.
Traditional perimeter protection is increasingly being circumvented
There is no question that firewalls as perimeter protection are still relevant for cybersecurity. However, they are becoming more and more just the first line of defense among many. The BSI's findings illustrate how essential a defense-in-depth architecture is becoming for industrial companies.
- Attackers are increasingly trying to penetrate networks via legitimate access points.
- Optimized and highly diversified phishing campaigns continue to improve and are also targeting individuals on private channels. Phishing is no longer limited to business email (the proportion of which is actually declining). Vishing (voice, often in connection with identity theft from social media), quishing (QR codes in public spaces leading to malicious websites), smishing (SMS), and the enormously dynamic development of malicious websites (pages exist for less than two hours on average) have visibly increased the arsenal of phishing actors.
- The number of known vulnerabilities has risen again by a further 24% compared to the previous year. Infrastructure operators must now assume that a system or communication channel has a vulnerability per default.
- The number of exploitations documented in a BSI honeypot has risen by 38% to 1,081. Protocols that are still commonplace in OT networks were particularly targeted and exploited, including SSH (52%), RDP (22%), Telnet (11%), and VNC (10%). SSH is used for logins, while RDP and VNC play a crucial role in remote access to systems.
- Infected systems are on the rise, especially in the IoT sector. In two major incidents, botnet malware was even found pre-installed on devices.
As a result, signature-based intrusion detection is falling further and further behind. This is also accelerated by the use of large language models (LLMs). Claude's Anthropic seem to secretly think this to be really cool. In their article “Disrupting the first reported AI-orchestrated cyber espionage campaign”, they come across like 8-year-old boys celebrating their discovery that it feels funny when you stick your finger in a power outlet. You could almost think the text is a motivation letter to cybercriminals.
Cybersecurity is too slow in critical infrastructure
On the other side of the spectrum, however, things are moving at a sedate pace. The BSI's maturity assessment is cautiously optimistic. “The resilience of critical infrastructure is improving slowly but steadily. More and more critical infrastructure operators have reached maturity level 3 or higher,” writes the Federal Office in the section “Critical Infrastructure”.
However, more than 21% (ISMS) and 36% (BCSM) still remain at maturity levels 1 and 2, an improvement of just 2% and 1% respectively compared to the previous year. In individual sectors such as energy and water, companies appear to have even been downgraded when comparing 2024 and 2025.
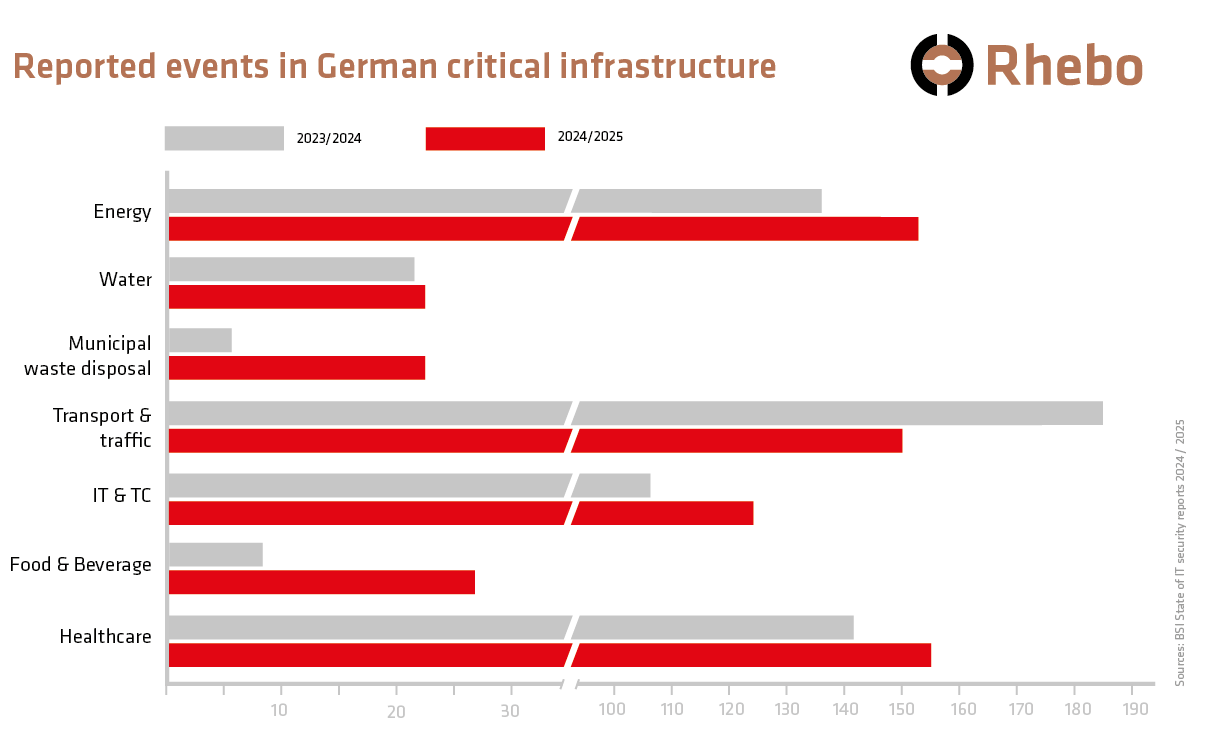
It should be noted that the obligation to implement holistic cybersecurity in their critical processes and systems has been in force for these companies for almost four years now thanks to the German IT Security Law (IT-SiG 2.0)! And the attackers are not waiting around. On the contrary, reported incidents in critical infrastructures have risen considerably in some cases (Fig. 1).
What companies with OT ought to look into now
Companies with OT systems and networks ought to start by assessing the attack surface of their own infrastructure:
- Are devices accessible from the internet?
- What misconfigurations exist?
- What open vulnerabilities exist?
- Are communication flows secure?
- How is access to equipment and systems secured?
- Has the network already been compromised?
A Rhebo Industrial Security Assessment examines the OT in detail for such existing vulnerabilities and security risks. It locates them and analyzes them, and provides recommendations to fix them. In addition, a pentest provides information about further loopholes and organizational security gaps.
The second step is to check whether the OT is sufficiently integrated into the cybersecurity infrastructure. Since 2019, the BSI has recommended security monitoring in production networks. At the beginning of 2025, both the BSI and the US NERC confirmed that a network-based intrusion detection system (NIDS) is an efficient and important tool for station automation to detect attacks at an early stage, especially if they use unknown signatures.
