In the first part of this blog post, we mapped the general functions of an intrusion detection system (IDS) according to internationally accepted definitions to possible solutions. This article highlights the additional recommendations for an IDS by national cybersecurity authorities.
For starters, there are little details regarding the functionality of an IDS or NIDS (network intrusion detection system) that are not defined by solution providers.
The most detailed description of what an intrusion detection system shall be made of, is provided by the German Federal Ministry of Information Security (or BSI) that released a guidance with several dozens of requirements in regards to logging, detection and reaction.
Furthermore, the North American Electric Reliability Corporation (NERC) published a Critical Infrastructure Protection Reliability Standard in 2025, defining the functions of a network monitoring system that basically is equivalent to a network intrusion detection system (NIDS) introduced in the first part of this blog series. It is interesting to note that the authoritative National Security Agency (NSA) recommends NIDS only for monitoring inbound and outbound traffic 1, completely underestimating / misunderstanding the working and objective of a NIDS.
So, let’s have a look at the BSI and NERC guidelines.
BSI guidance on intrusion detection systems
In its "Orientation Guide to Using Intrusion Detection Systems (IDS)” 2, the BSI defines the basic requirements for a compliant IDS. It should be mentioned, that the BSI does not limit its guidance on technologies and their features but includes organization and processes as well. This will not be considered here.
In technological terms, an intrusion detection system must have the following basic functions:
- Identify relevant OT systems and create visibility in the OT: This points in direction of a passive network intrusion detection system (NIDS) that can identify and document relevant OT systems by detecting their communication pattern. If possible (e.g. during maintenance cycles), an active network scan via an inventory mapping system might be reasonable.
- Continuously monitor and evaluate logging data at the system AND network level and store security-relevant events (SREs): While the network level can be covered by a NIDS only, the device level provides two options. One are host-based intrusion detection systems though this might be restricted to IT systems within the OT due to limited CPU. The other option are existing logs provided per default by respective components.
- Detect and report SREs, even if they do not follow known signatures: This summarized all available detection methods – signature-based (firewall) and anomaly-based (NIDS, SIEM) – highlighting the multi-level approach by the BSI.
- Correlate SREs: Correlation is generally done with a Security Information & Event Management (SIEM) system where all data sources are aggregated,
- Enable a qualified response within a reasonable time: Incident response starts with correct and detailed information on the incident as provided by a NIDS and follows up with well-informed decisions. Most importantly, this requires clear responsibilities and processes.
- Regularly check the different security measures and optimize functionalities: This can be achieved by two supplement perspectives. First, the anomaly alerts might indicate security gaps of the existing “1st line of defense” mechanisms. Second, regular security audits and vulnerability assessments provide an objective 3rd party view on the existing security posture.
Again, this condensed list makes clear how the individual tools work together rather than excluding each other.
Rhebo has created a mapping for the OT area that shows how our solutions meet or support the individual requirements according to the BSI guidance (see poster).
NERC CIP-015 on Network Monitoring Systems
In June 2025, NERC published the first edition of its standard CIP-015-1 “Cyber Security – Internal Network Security Monitoring” 3.
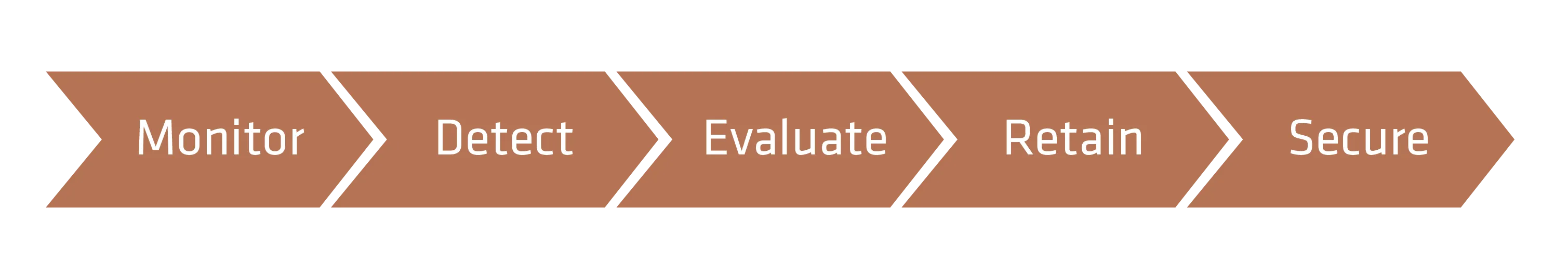
This standard makes it mandatory for companies operating in the energy sector to establish and operate a network monitoring system with the following capabilities:
- Network data feed(s) to monitor network activity; including connections, devices, and network communications (R1.1): This would entail data collectors integrated via mirror-port switches or network taps (hardware solution) or on existing security gateways (software solution). All three options are available for Rhebo Industrial Protector. Additionally, existing device logs should be used as a source.
- One or more method(s) to detect anomalous network activity using the network data feed(s) (R1.2): This would rule out any system that only uses signature-based detection. The network security monitoring tool needs to have integrated anomaly detection like the NIDS Rhebo Industrial Protector. The anomaly detection should be able to analyze both, IT and OT protocols found in OT networks.
- One or more method(s) to evaluate anomalous network activity detected in Part 1.2. to determine further action(s) (R1.3): This can be done directly in the network security monitoring tool (e.g. with risk scoring and pcaps) and/or – to get a more contextual and harmonized evaluation of OT alerts – within a SIEM system. Rhebo Industrial Protector provides both options.
- Process for retaining the monitoring data (R2): As an example, Rhebo Industrial Protector provides all information on incidents as downloadable Packet Captures (pcap).
- Process to secure monitoring data (R3): This can be implemented via restrictive roles and privileges.
It is also worth reading NERC’s “Technical Rationale for Reliability Standard CIP-015-1" published in February 2024.
In a nutshell: The BSI and NERC guidance both define a NIDS (i.e. a network monitoring with anomaly detection) as an integral part of an effective overall intrusion detection system.

1 NSA: Network Infrastructure Security Guide, 2023
2 https://www.bsi.bund.de/SharedDocs/Downloads/EN/BSI/KRITIS/oh_sza_en.html
3 https://www.nerc.com/pa/Stand/Reliability%20Standards/CIP-015-1.pdf (direct pdf download)
