The situation of OT cybersecurity remains challenging in 2025. Although only a few attacks - compared to the total number of cyberattacks - targeted industrial facilities directly in 2024, the attack surface continues to evolve.
At the same time, many industrial companies are still in the early stages when it comes to a structured and effective OT cybersecurity strategy. Rhebo has summarized the developments in OT cybersecurity in its report “The State of OT Cybersecurity – Metrics and trends from global to local” and expanded it with insights from hands-on experience with customers.
Global: OT security is increasingly critical to the system
In 2024, targeted attacks on OT networks were still the exception. Nevertheless, the figures show that cyber incidents in IT are increasingly affecting physical processes due to spill-over into OT (Fig. 1).
According to statistics, 76 documented attacks had an impact on physical OT processes. However, due to the strong interconnectedness within the affected companies, around 1,000 facilities were affected. At the same time, the informative value of pure reporting statistics is severely limited. A lack of reporting requirements in many countries, nations without public publication, and companies' concerns about actually reporting incidents (in detail) unavoidably mean that the number of unreported cases is likely to be high.
It is also questionable what can be detected in IT and OT by cybersecurity tools, which are often still conventional. This is because attackers are increasingly utilizing stealth tactics using amongst others living-off-the-land techniques, zero-day vulnerabilities or stolen access data. Additionally, in just one year, three new OT-capable malware programs were discovered: FrostyGoop, IOControl and Fuxnet.
What's more, “prepositioning” campaigns made public by CISA and intelligence agencies show that the aim is no longer just immediate sabotage, but also long-term strategic positioning in networks.

Europe: Regulation meets business practice
Regulation is picking up speed in the EU: NIS2 and the Cyber Resilience Act require over 400,000 companies to implement cybersecurity measures. However, implementation is slow. Many companies are struggling with limited staff, a lack of expertise and limited budgets.
There are also technical weaknesses: vulnerabilities in supply chains, attacks via remote access and a lack of transparency in the components used are widespread (not only in Europe). ENISA continues to classify the cyber risk for Europe as “substantial”. Over 3,000 cyber attacks hit industrial companies in 2024 (Fig. 2).
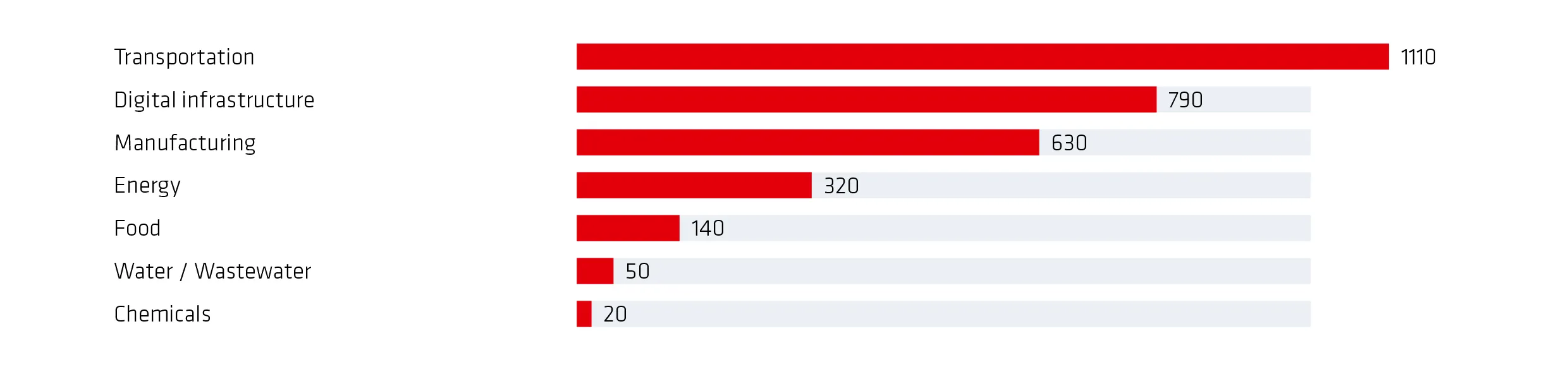
Germany: High adversary density and implementation gaps
Last year, a total of 144 different adversaries carried out cyberattacks on German companies and private individuals. This puts Germany in second place worldwide after the USA. Of these active adversaries, the BSI classified 22 as advanced persistent threats.
A total of 726 security incidents were reported to the BSI by the critical sector – many of them in the energy, transport and water sectors. Nevertheless, according to the BSI, only 31% of operators of critical infrastructures in these sectors have met all the MUST requirements for an intrusion detection system (IDS), even though this has been mandatory since 2021.
OT networks in reality check: What risk assessments reveal
Practice confirms what the numerous reports reveal: there are few actual attacks, but most OT networks are poorly prepared should attackers shift their focus from IT to OT in the future.
Rhebo has analyzed numerous OT networks as part of Rhebo Industrial Security Assessments. The results show that fundamental vulnerabilities persist (Fig. 3), including:
- outdated or insecure protocols,
- broken authentication methods,
- insecure systems and software,
- unauthorized or unnoticed internet connections.
These security risks do not necessarily pose an immediate threat, but they do open up potential attack surfaces. And they show how great the need is for visibility and monitoring of legacy systems.

BSI President Claudia Plattner recently put her finger on the tensions in which critical infrastructure and industrial companies find themselves in a LinkedIn post: "Criminal groups today often act on behalf of a state. [...] Once an adversary is in the system, unfortunately it's often just two clicks from espionage to sabotage. It's even more dangerous when digital product makers have ongoing access to the systems their customers have installed, for example through regular updates." The quiet of recent years in OT could very quickly change
.
On the path to OT security: clarity, resources, systematics
The good news is that many companies want to actively improve their OT security.
But to get there, they need:
- visibility and transparency of systems and communication flows.
- technological understanding of OT-specific risks and vulnerabilities.
- reliable processes for detecting and assessing security incidents.
- partnership-based support for analysis, monitoring and learning-on-the-job.
In many cases, it is not so much a lack of will – but rather a lack of clarity on how and where to start.
Do you want to know where you stand?
A Rhebo Industrial Security Assessment provides initial visibility and transparency of your OT risk exposure – and forms the basis for all further measures. We are happy to support you in this.
