
OT risks - Findings from vulnerability assessments #2:
OT risks - Findings from vulnerability assessments #2: The Top 10 security risks
Apr 15, 2024
5 min

We have already addressed the problem of a lack of visibility in OT in the first part of this trilogy. It is also the main reason why even the most obvious security vulnerabilities in OT networks remain undetected for a long time.
In addition to the lack of visibility, the top 10 also point to two other problems that are specific and typical for OT:
- OT networks are often evolved structures in which unconventional solutions and, above all, quick fixes are implemented to ensure process stability. Often, these ad-hoc changes were not documented in a standardized way. In addition, no special security precautions were implemented in the formerly air-gapped OT in the past. As a result, internet-capable or fundamentally insecure systems may have been integrated in the past without any concerns. Today, they suddenly pose a huge (but mostly unknown) security risk due to IT/OT integration.
- Due to the long life cycles of industrial infrastructures, there are many legacy systems, servers and protocols in OT. These can often neither be patched nor simply replaced - either because there is no support from the manufacturer any longer or because a change would jeopardize process stability. These legacy components can still be moved to separate subnets, i.e. segments, in order to limit the risk and access to them, but ultimately they must be monitored continuously.
The ten most common security risks in OT in 2023
The top 10 security risks identified in Rhebo Industrial Security Assessments 2023 reflect these fundamental problems of OT networks.
Insecure authentication methods were already high up in the top 10 in 2022. These differ from non-encrypted password transmission in that the method is so old that it can be breached by the simplest means, even with existing encryption.
Outdated operating systems, servers, firmware, software and protocols can indicate both a lack of patch management and infrastructures that have been in operation for 10-15 years or more - and therefore contain a lot of legacy.
Successful and attempted internet communication from OT systems to IP addresses outside the company network was also detected very frequently. Factory settings of systems and misconfigurations are often the cause of this risk. They offer attackers the opportunity to collect information about systems used in a company's network, configurations and - in conjunction with unencrypted password transmission - system credentials.
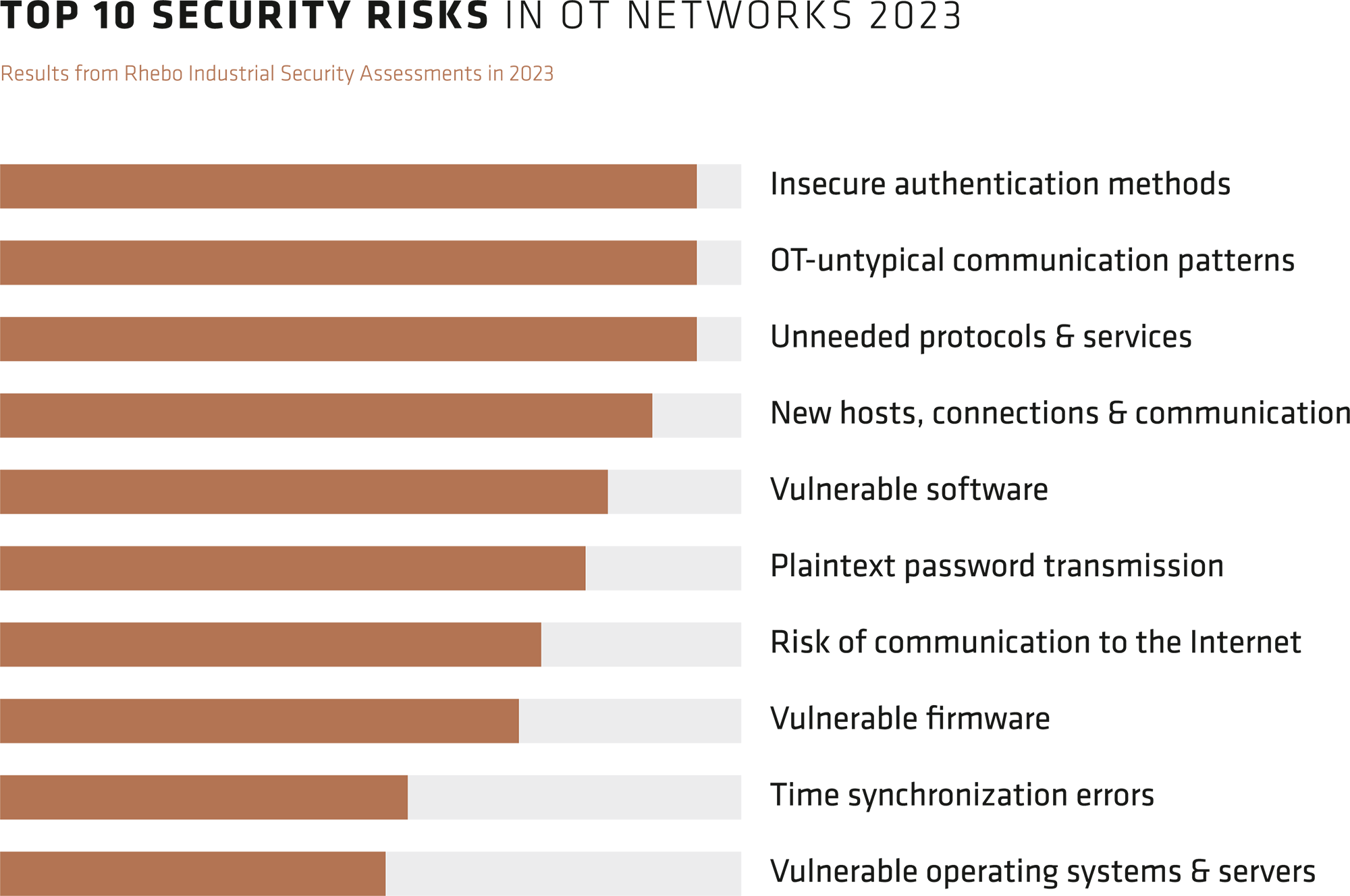
Close-up view: new hosts, connections and communication
This category includes three events that typically occur during attacks. For this reason, this top category is one of the most important in the ongoing operation of an OT intrusion detection system.

New hosts can be smuggled-in devices in the OT or remote devices that are used for further attacks after a successful network access (e.g. command-and-control servers).
New connections to other devices in the OT are subsequently established via these new hosts, but also via compromised devices within the OT. This is used for lateral movement, threat propagation, establishing persistence and further information collection within the network.
During an attack, the compromised devices usually establish new communication, i.e. the use of new protocols or functions not previously used between the two hosts.
Close-up view: OT-untypical communication patterns
OT-untypical communication patterns often lie at the interface of security and availability, i.e. malicious communication changes and technical error states in the network.
This category typically includes changes in a host's communication behavior for a specific connection or specific protocols. These changes can include:
- very short-term, usually one-off communications,
- short, irregular peaks or collapses,
- changes in the frequency of communication,
- complete communication breakdowns.

All of these changes are atypical for the deterministic, repetitive communication that prevails in OT networks and should therefore be observed and analyzed more closely.
In part 3 of this blog series, we analyze the top 5 technical error states that we have identified in the vulnerability assessments of our customers' OT networks and which endanger process availability.
Latest posts
All news directly to your inbox.
Sign up now for the Rhebo newsletter.