The media regularly warns of the impending cyber threat to industrial networks, or OT (Operational Technology). At the same time, voices regularly soothe the fears of critical infrastructures and industrial companies by pointing out that there have only been a handful of direct attacks on OT networks to date. While these voices are right in retrospect, looking forward, the question is no longer whether OT will be attacked, but only when.
In the following three blog posts in our series "OT risks - findings from vulnerability assessments 2023", we provide insights into the true risk status of many OT networks. The findings come from several dozen OT vulnerability assessments and risk analyses. The Rhebo Industrial Security Assessment is carried out at our customers' premises both before the introduction of the OT network intrusion detection system Rhebo Industrial Protector and repeatedly as part of service level agreements under Rhebo Managed Protection.
Rhebo Industrial Protector is integrated into the investigated OT network within a few minutes. Passive OT monitoring then records the communication for ten to 14 days during normal OT operation. This recording (pcap) is then examined in detail by our experts for existing OT risks in terms of both cyber security and availability.
From our point of view, the results tend to prove the cautioners correct rather than the appeasers. Nothing has changed in this respect since our evaluation last year.
Let’s open the OT black box
A first look at the OT shows that the structure and variability is relatively clear, at least on average. At just over 30, the main protocols used are far below the number known from IT. The number of different manufacturers also remains manageable, although the average number of 16 is not negligible.
The number of hosts (i.e. individual devices and systems) depends heavily on the size of the infrastructure examined. Depending on this, between just under 40 and over 520 devices were identified, an average of 178 per OT network. However, in one exception (which was not included in the average due to being an outlier), over 6,000 devices were found in a single OT network.
At first glance, the overall complexity of the OT networks is limited. It is therefore not the problem faced by security officers. A lack of visibility, missing or neglected security guidelines and the often incomplete documentation in OT networks pose the real risk, regardless of the number of devices, manufacturers and protocols in the network. During Rhebo Industrial Security Assessments, we have often found devices, protocols and communication in OT that neither operators nor security managers knew anything about.
Security risks dominate
The question of why it is not "if" but "when" that makes up the decisive perspective in OT cyber security is illustrated by the number of risks and anomalies that we found in OT networks.

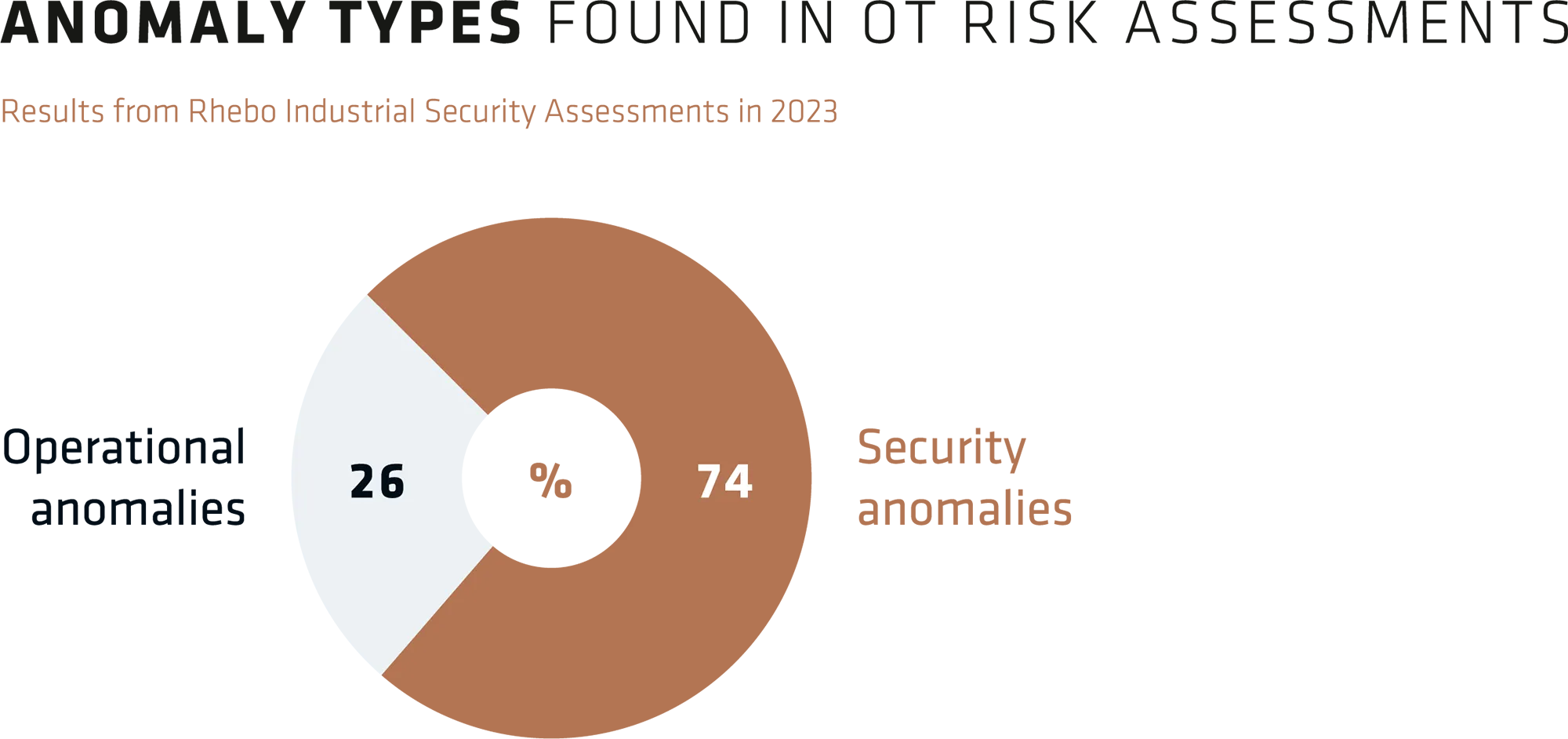
On average, 26 different anomaly types were identified as part of the Rhebo Industrial Security Assessments. Anomaly types describe categories of detected anomalies. For example, in the case that "insecure firmware" was found in an OT network, this was only counted once for the present statistical evaluation, even if several different insecure firmwares were found. The number of individual anomalies is therefore much higher.
The majority (74%) of the anomaly types identified can be assigned to the area of cyber security. The remaining 26% represent aspects of network quality and network availability - i.e. anomaly types that can lead to network failures and process errors.

In the second part of this trilogy, we look at the security risks that make up the majority of anomalies hidden in OT networks.
Part 3 concludes with a look at availability risks.
